[ad_1]
IBM recently patched a vulnerability in IBM Cloud Databases for PostgreSQL that could have exposed users to supply chain attacks.
The vulnerability has been named Hell’s Keychain by cloud security firm Wiz, whose researchers discovered the issue. It has been described by the company as a “first-of-its-kind supply-chain attack vector impacting a cloud provider’s infrastructure”.
“The vulnerability consists of a chain of three exposed secrets (Kubernetes service account token, private container registry password, CI/CD server credentials) coupled with overly permissive network access to internal build servers. This attack vector could allow malicious actors to remotely execute code in customers’ environments to read and modify the data stored in the PostgreSQL database,” Wiz said.
The exposed secrets could have been leveraged by an attacker to access IBM Cloud repositories that store software dependencies for PostgreSQL container images. The attacker could have altered trusted repositories and forced users’ PostgreSQL instances into running malicious code.
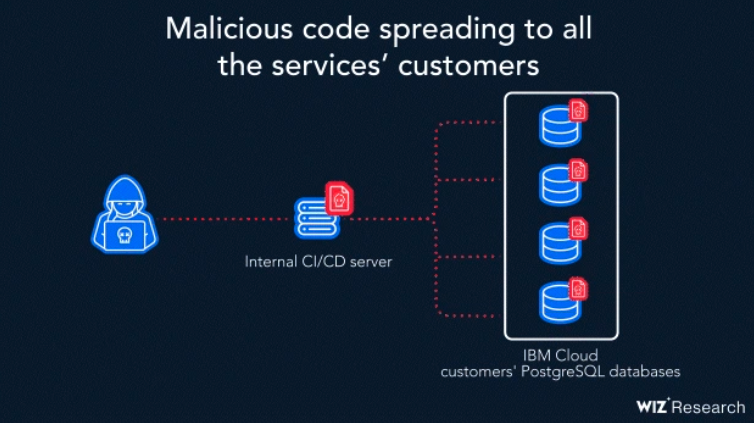
IBM said in its advisory that the flaw has been patched and customers do not need to take any action as the fixes have been automatically applied. The tech giant has found no evidence of malicious exploitation.
The security hole has not been assigned a CVE identifier — as is typical for cloud vulnerabilities — but Wiz does maintain a database of vulnerabilities and other security issues affecting cloud services.
Wiz has published a blog post providing a detailed technical description of Hell’s Keychain.
“Hell’s Keychain reinforces the importance of proper secrets management, network controls, and tenant isolation, especially in large and complex cloud environments,” the cloud security firm said.
Related: Oracle Cloud Infrastructure Vulnerability Exposed Sensitive Data
Related: IBM Patches High-Severity Vulnerabilities in Cloud, Voice, Security Products
Related: ‘Sysrv’ Botnet Targeting Recent Spring Cloud Gateway Vulnerability
[ad_2]
Source link




