[ad_1]
Learn what the expanded cloud offerings mean for potentially smoothing out the line between DevOps and SecOps.

IBM continues to expand its cloud offerings with Hybrid Cloud Mesh, a software-as-a-service platform meant to give DevOps and CloudOps teams more fine-grained control over application connectivity between clouds. It could be a way to remove silos and speed up network management. In addition, Hybrid Cloud Mesh takes advantage of the recent acquisition of network automation company NS1.
Hybrid Cloud Mesh will be available later in 2023, IBM said, and ut is currently part of an early access program.
Jump to:
What IBM Hybrid Cloud Mesh does
IBM says Hybrid Cloud Mesh is an on-ramp and management portal for apps and services across multiple, different environments. It can bring secured application connectivity across clouds in minutes, not days. If an organization finds itself running operations across multiple clouds, Hybrid Cloud Mesh can connect them. IBM Hybrid Cloud Mesh can be used at the beginning of an organization’s digital transformation to put a flexible framework in place for their planned ground-flood cloud deployment.
In cases where infrastructure is located across a wide geographic swath, IBM Hybrid Cloud Mesh can visualize connections between application-centric resources (Figure A).
Figure A
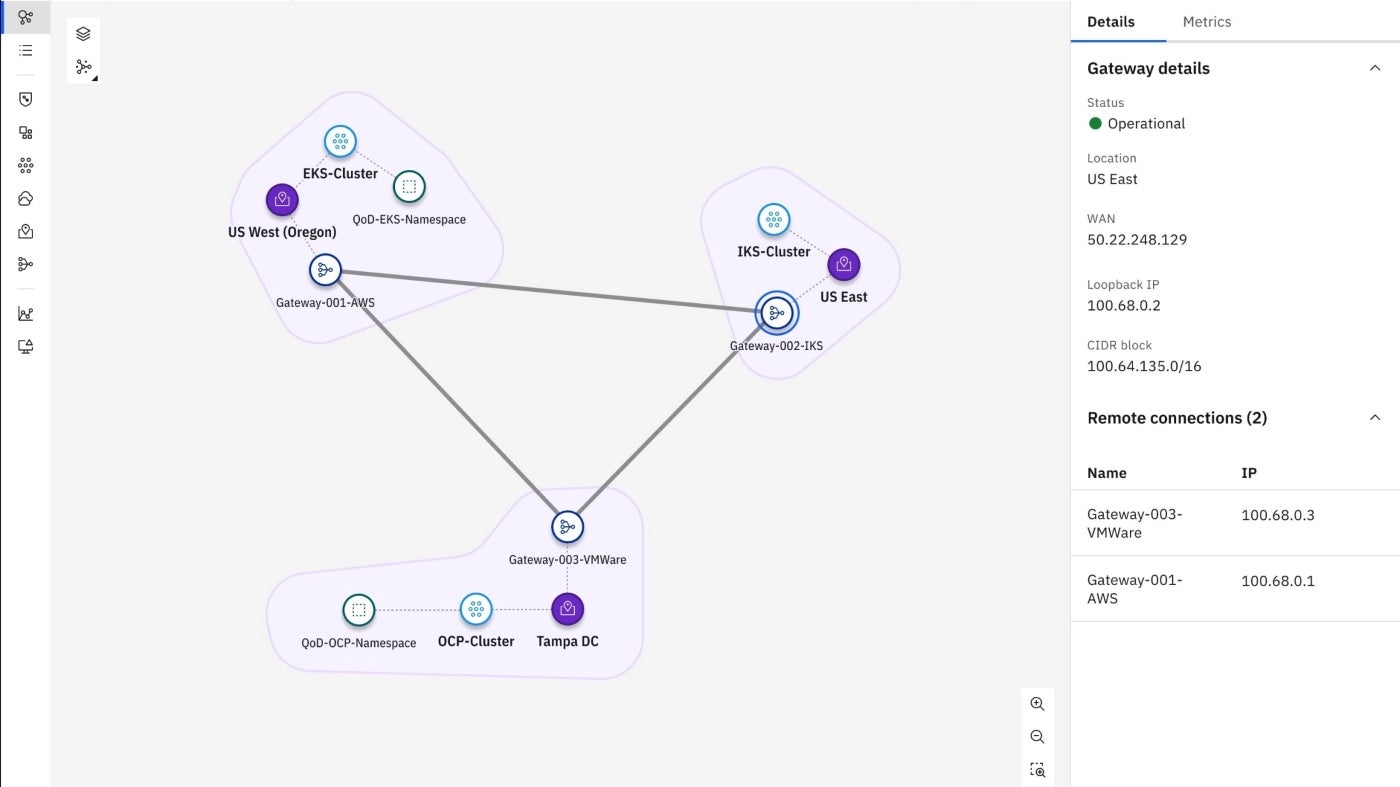
IBM Hybrid Cloud Mesh shifts how businesses use multicloud
Another way IBM explains Hybrid Cloud Mesh can increase efficiency is that an operations team can instruct the network to “follow the application” when services move across locations, streamlining app migration. It can auto-discover cloud infrastructure and applications in order to speed up the process. Further, IBM Hybrid Cloud Mesh lets DevOps and CloudOps teams work in a single portal.
Right now, managing application connectivity across multicloud environments can take days; by giving CloudOps and DevOps access to the same infrastructure at the same time, IBM hopes to handle it in minutes. The two teams can work at the same time, or the CloudOps team can put their work in ahead of when DevOps needs to set rules and parameters.
“In the process, we’ve vastly simplified the process and steps it takes to connect clouds together and made the experience the same, regardless of which cloud you are connecting to,” Andrew Coward, general manager of software defined networking at IBM, told TechRepublic. “This increase in velocity and business agility significantly cuts down CloudOps timeline for deployment and reduces the friction with DevOps.”
SEE: Applying for a project management job in DevOps? See common interview questions and how to answer them.
Many enterprises today use a mix of public and private clouds as well as edge devices, according to an IDC study cited by IBM. In addition, 76% of network data will be created and processed at the edge. Applications and data assets may be widely spread across clouds.
Tearing down silos
Removing silos between development, security and operations teams has long been a point of conversation in the industry. With Hybrid Cloud Mesh, IBM hopes to provide “granular network control to CloudOps teams and easy-to-consume interfaces for DevOps teams,” Coward said.
All of these teams working in the same platform will allow clearer conversation around security, network resources, connectivity and performance metrics, he proposed.
“Enterprises can mitigate the significant strain that their infrastructure and operations teams feel when deploying, managing and securing their hybrid multicloud networks in an era with increasingly limited control and visibility,” Coward wrote.
IBM Hybrid Cloud Mesh takes advantage of DNS traffic steering capabilities
Following its acquisition of NS1 in February 2023, IBM will use NS1’s DNS traffic-steering capabilities to enhance Hybrid Cloud Mesh. NS1’s network automation solutions will let IBM choose the best connection between a client’s clouds and end users more easily. This enables more options for applications optimized for performance, cost and availability across all of their connection points, IBM said.
Next, IBM plans to add more features, including the ability to to automatically optimize network traffic. IBM Hybrid Cloud Mesh will be able to monitor business intent, applications needs and connection performance. By feeding that information back to operations teams in the form of traffic engineering recommendations, it can add even more efficiency to cloud management, IBM said.
Competitors
Big Blue is one of a crowded field of organizations trying to smooth out cloud operations. Rivals and alternatives include Dell’s APEX Cloud Services, Amazon Web Services, Oracle Cloud Services, iland cloud from 11:11 Systems, OpenStack’s cloud infrastructure services, Google’s Cloud Platform and more.
[ad_2]
Source link



