[ad_1]
Fast food giant Wendy’s says that it now believes that more than 1000 of its restaurants across the United States have fallen victim to a hacking gang, who used malware to steal customers’ credit and debit card information.
Fast food giant Wendy’s says that it now believes that more than 1000 of its restaurants across the United States have fallen victim to a hacking gang, who used malware to steal customers’ credit and debit card information.
In a statement posted on Wendy’s website, president and CEO Todd Penegor apologises to affected customers, and explains that the company has been investigating the data breach since earlier this year:
Wendy’s first reported unusual payment card activity affecting some restaurants in February 2016. In May, we confirmed that we had found evidence of malware being installed on some restaurants’ point-of-sale systems, and had worked with our investigator to disable it. On June 9th, we reported that we had discovered additional malicious cyber activity involving other restaurants. That malware has also been disabled in all franchisee restaurants where it has been discovered. We believe that both criminal cyberattacks resulted from service providers’ remote access credentials being compromised, allowing access – and the ability to deploy malware – to some franchisees’ point-of-sale systems.
Wendy’s believes that the malware has been effectively deployed on some franchisee systems since late fall 2015, stealing the following payment card data: cardholder name, credit or debit card number, expiration date, cardholder verification value (different from the three digits on the back of your card), and service code.
Of course the longer malware lies undetected on a retailer’s systems, the more information it can potentially steal.
Although Wendy’s has declared that at least 1,025 restaurants have been hit by the hackers it has not said publicly how many customers it believes might be impacted by the data breach.
The use of malware to infect point-of-sale (POS) systems at retailers is something we have seen more and more in recent years, with a variety of stores and hotels forced to confront attackers that have used sophisticated surreptitious malware to intercept credit card details.
And the fact that Wendy’s is pointing a finger of blame towards the hackers gaining access to their network via a third-party provider’s login credentials will surely ring a bell in the memory of those who recall the monumental hack against Target – whose network was breached after login credentials were stolen from an HVAC subcontractor.
If Wendy’s suspicion that the attacks were assisted by the hackers exploiting the usernames and passwords of third-party service providers then there is a clear message for all businesses:
- If you must give service providers access to your network, insist upon strong password policies (for instance, unique, hard-to-crack passwords for each login) and additional levels of authentication to reduce the chances of hacker exploitation.
- Even if you trust your service provider, limit what they can do on your network – keeping access to the absolute minimum that they require to do their job.
- Have systems in place to monitor who accesses your network, what data they access, and have it report suspicious or unusual activity so it can be investigated.
- Require your third-party suppliers and partners to comply with baseline security procedures. If you don’t feel confident that they can meet your standards, don’t give them access to any part of your network.
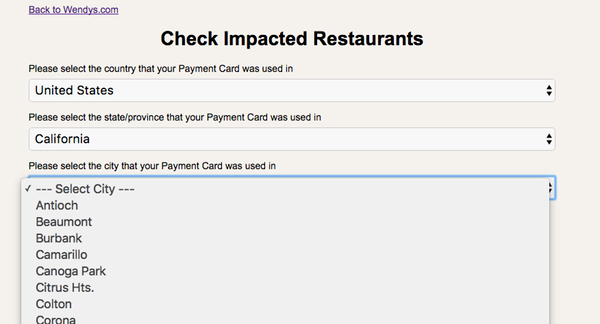
Of course, you are probably wondering if you might have been impacted by the breach. Fortunately Wendy’s has provided a webpage where you can easily choose your location from a drop-down list, and see if your local restaurant is one of those which is known to have been struck by the hackers.

Wendy’s is offering potentially impacted customers who paid with a card one complimentary year of fraud consultation and identity restoration services.
With so many big retailers falling foul of credit card-stealing hackers in recent years, you might be wise to pay in cash next time you fancy a burger.
[ad_2]
Source link