[ad_1]
A new research report from SentinelOne exposes a SEO poisoning attack campaign that hijacks brand names in paid search ads.

SentinelOne has reported an increase in malicious search engine advertisements in recent weeks. The researchers explain that attackers using search engine optimization poisoning are generally more successful “when they SEO poison the results of popular downloads associated with organizations that do not have extensive internal brand protection resources.”
Jump to:
What is an SEO poisoning attack?
SEO poisoning attacks consist of altering search engines results so that the first advertised links actually lead to attacker controlled sites, generally to infect visitors with malware or to attract more people on ad fraud. SentinelOne provided an example of a recent SEO poisoning campaign in their report.
SEE: Mobile device security policy (TechRepublic Premium)
The Blender 3D SEO poisoning campaign
A routine search on Google’s search engine for the brand name Blender 3D, an open-source 3D graphics design software, provided the following results on Jan. 18, 2023 (Figure A):
Figure A
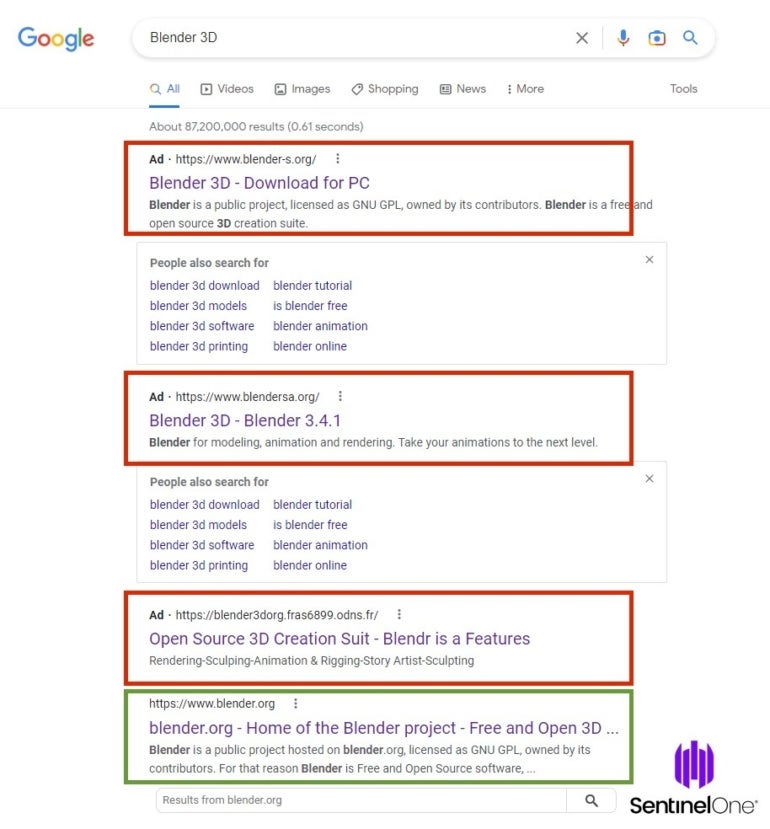
A user who doesn’t read the URL closely or is unsure of the exact URL of the software might click on any of those attacker-controlled domains, which could result in a compromise.
The malicious top result blender-s.org is a near exact copy of the legitimate website from Blender, yet the download link does not lead to a download on blender.org but to a DropBox URL delivering a blender.zip file.
The second malicious website at blenders.org is similar: It shows a near perfect copy of the legitimate Blender website, yet the download link leads to another DropBox URL, also delivering a blender.zip file.
The third and last malicious website is also a copy of the legitimate one, yet it provides a Discord URL and delivers a file named blender-3.4.1-windows-x64.zip.
The SEO poisoning payloads
The zip files which are downloaded from Dropbox contain executable files. The first one immediately raises suspicion as it shows an invalid certificate from AVG Technologies USA, LLC (Figure B) which has been already observed as being used by other malware including the infamous Racoon Stealer.
Figure B

It is also worth mentioning that the zip file has a size that is less than 2 MB, but the executable file extracted from it is close to 500 MB. This is probably an attempt to bypass some security solutions who do not analyze such big files.
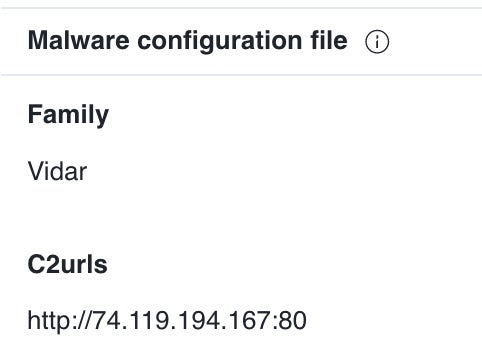
According to VirusTotal, the malware might be the Vidar malware (Figure C), an information stealer with the ability to steal financial information, passwords and browsing history from browsers, password managers and cryptocurrency wallets.
Figure C
The second zip file, unknown to VirusTotal, might be similar, as the zip file has the same size and has been created five minutes after the first one. The final file, downloaded from Discord, contains an ISO file that is probably also malicious.
Widening the attack surface
According to SentinelOne researchers, the threat actor behind the first two malicious websites are also responsible for dozens of other similar websites, always impersonating popular software such as Photoshop or remote access software.
All of those websites were quickly blocked by CloudFlare, whose services were used by the cybercriminals. Any user attempting to connect to the fraudulent websites is now shown a warning page from CloudFlare mentioning their phishy nature.
How to mitigate this threat and protect your company’s reputation
As mentioned, SEO poisoning attackers usually choose to impersonate popular products or brands in order to run their malicious operations. This has a huge impact on users, as they might end up being compromised by malware, which can lead to stolen data. Yet it also has a huge impact on companies, as the average user often does not understand this kind of fraud and in the end thinks that the real brand is responsible.
Companies with very popular products or brands should be careful about their brands and deploy security solutions to help them detect such fraud before it’s too late.
For starters, organizations should carefully check every new domain that is registered on the Internet that contains similarities with any of their brands or names. As fraudsters often register domain names that are very similar to the legitimate ones, it is possible to detect them within 48 hours in most cases, immediately analyze the situation and take action to mitigate the risk.
Companies can work on the legal side to have the fraudulent domains transferred to them when they can justify that a trademark infringement exists, but that might take a while. In the meantime, should any fraudulent content appear on the fraudulent domain, they might want to shut it down by contacting the hosting company, registrar or DNS provider to render the fraud unreachable.
Finally, companies can preventively register different variants of their legitimate domain names so that fraudsters can’t do so. However, this method takes energy and money, and not every company may want to go down this path.
Disclosure: I work for Trend Micro, but the views expressed in this article are mine.
[ad_2]
Source link



