[ad_1]
Okta’s formula for multi-device identity authentication for a hybrid workforce: extract passwords, add ease of passkeys across devices.

Amid an industry migration away from passwords, Okta has launched Okta Device Access, part of its suite of Workforce Identity Cloud products and an effort to unify passkey access across all devices under a single identity and access management platform. With the new feature, Okta aims to appeal to organizations dealing with security headaches caused by a hybrid workforce using devices outside of the security perimeter.
Designed to extend identity access management to the point of device login, the Okta Device Access service is also meant to reduce the likelihood that users, faced with the aggravation of having to wrangle repeatedly with logins for each device, will jettison security protocols.
The new capabilities include desktop-based multi-factor authentication for both Mac iOS and Windows, as well as a desktop password sync for MacOS. The latter gives local macOS users Okta credentials and enrolls users into Okta Verify and FastPass, according to Okta.
Authentication through FastPass, MFA, Privileged Access
The overarching Workforce Identity Cloud portfolio includes passwordless authentication and access management through Okta’s FastPass, Device Assurance, Multi-Factor Authentication, and Privileged Access products.
According to Okta:
- For organizations requiring passwords, the new system lets users log in with an Okta password.
- The new product includes automatic enrollment in the Okta Verify mobile app.
- Okta Device Access includes the use of the FastPass passkey authenticator that automatically logs users into all of their apps.
The product allows MFA for Windows and macOS, including for desktop devices, to enable zero trust in order to put a wall around locally cached data, apps and non-internet-facing services that are stored on desktops.
It also enables desktop password sync for macOS, which Okta developed with Jamf and built on top of Apple’s Platform Single Sign-On Extension. The company said the feature securely provisions local macOS user accounts with Okta credentials while enrolling users into Okta Verify and its passkey authenticator FastPass.
Okta also said organizations can incorporate relevant device context into their authentication flows and gain higher security assurance through its Device Assurance capabilities in Okta Verify.
The new feature includes a user interface that appears native to the device (Figure A).
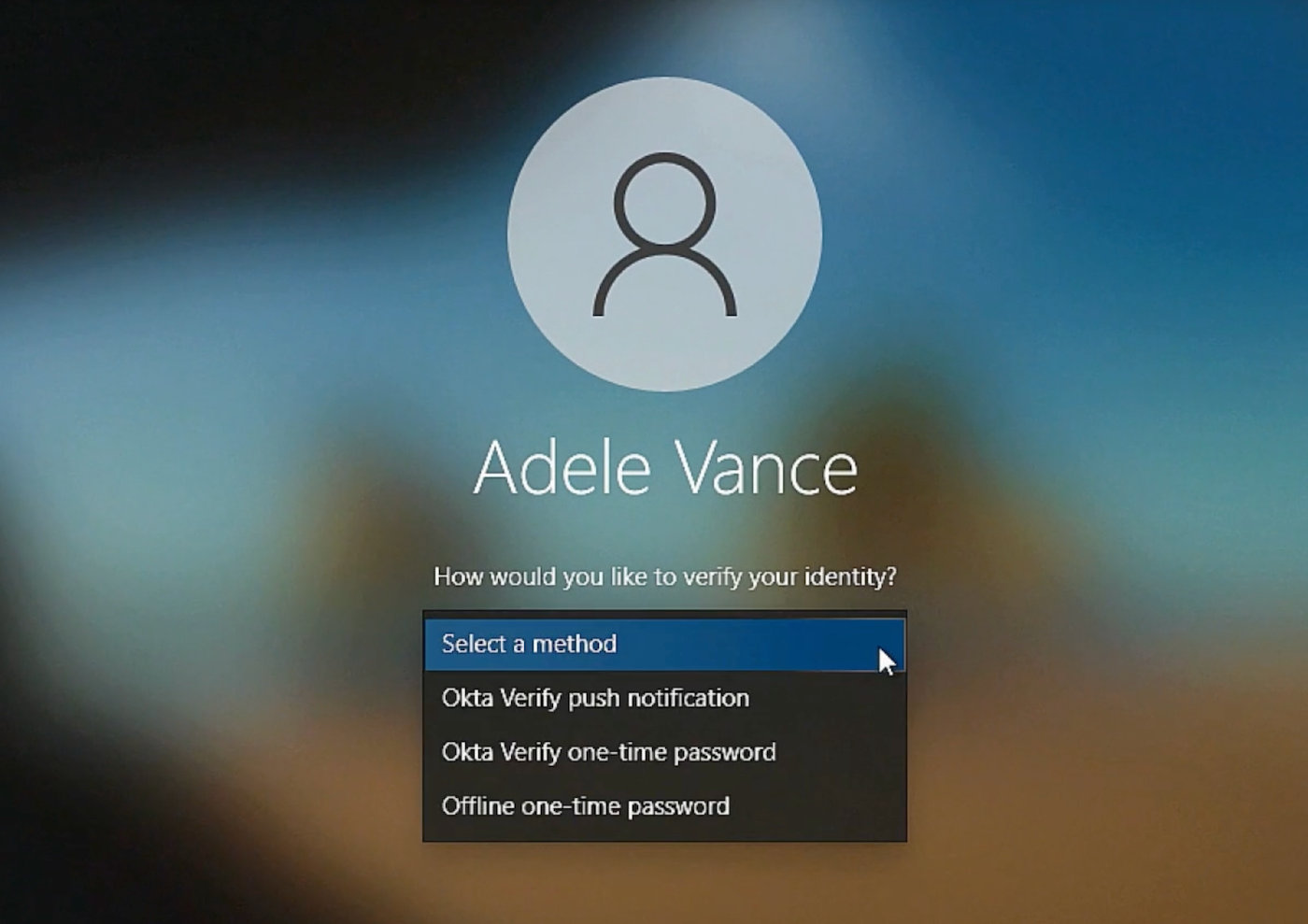
The user interface of Okta UX for Okta Device Access. Image: Okta.
Verizon’s 2023 Data Breach Investigation Report found that 49% of breaches involved stolen credentials. The report also found that 74% of all breaches include the human element, with people being involved via either error, privilege misuse, use of stolen credentials or social engineering. Also, Verizon’s study noted 2,091 incidents of lost or stolen devices, with 159 of these resulting in data breaches.
SEE: Verizon also noted (and presaged) the huge increase in DDoS attacks. (TechRepublic)
Last month, Google, Apple and other web services introduced passkey authentication. Identity authentication manager 1Password this month began enabling a raft of passkey capabilities that will continue to roll out next month and later this year.
The FIDO Alliance, which helped usher in the use of passkeys through the standardization of authentication cryptographic key protocols, articulates three key benefits conferred by passkeys:
- Consistency of user experience across devices, particularly when paired with biometric authentication.
- Passkeys are based on FIDO Authentication, which is proven to be resistant to the threats of phishing, credential stuffing and other remote attacks.
- Users do not need to enroll a new FIDO credential on each service or each new device (which would typically be with a password for that first sign-in).
Arnab Bose, the chief product officer of Workforce Identity Cloud at Okta, said that the solution is designed to help organizations reach zero trust while simplifying the log-in experience for employees.
“Identity has become the first line of defense in a hybrid world of cloud applications and devices,” he said. “We’re investing meaningfully to become a first-party player in the device security space and provide our customers with a unified authentication experience from any device to all applications. This empowers our customers to implement zero trust and use any technology safely.”
SEE: Okta study looks at long tail of consumer data trails (TechRepublic)
Availability begins Q3 of 2023
The company provided more details about Okta Workforce Identity Cloud’s release.
- Desktop MFA for Windows is planned to be in early access in Q3 of 2023 and generally available in Q4 of 2023.
- Desktop Password Sync for macOS is planned to be in early access in Q3 of 2023 and generally available in Q4 of 2023.
- Desktop MFA for macOS is planned to be in early access in Q4 of 2023 and generally available in Q1 of 2024.
[ad_2]
Source link



