[ad_1]

The Moscow-based cybersecurity company Kaspersky says iOS devices are being targeted by a previously unknown malware. The firm discovered the threat while monitoring the network traffic of its own corporate Wi-Fi.
Kaspersky is calling the new campaign Operation Triangulation. The campaign report reveals how the attack works and details the exploitation’s technical properties. Kaspersky’s researchers assure the oldest trace of infection dates back to 2019, with attacks still ongoing as of 2023 and affecting versions up to iOS 15.7.
Kaspersky’s zero-click attack report has caused controversy, as the Russian Federal Security Service claims thousands of Russians, including foreign diplomats and government officials, were targeted and compromised by the malware. Russia’s Federal Security Service has accused Apple and the U.S. National Security Agency of masterminding the attacks; Apple has denied this claim.
Jump to:
How this zero-click attack works
The new iOS security vulnerability is a zero-click attack. Unlike most malware attacks that require users to take action, like download a file or click on a link, zero-click attacks are self-executable, requiring no action from the users.
Kaspersky reconstructed the infection sequence by analyzing its compromised mobile devices’ timeline.
The attack begins when the targeted iOS device receives a message via the iMessage service. The message sent will include an attachment, which contains the exploit. With no interaction from the user, when the message is received, it triggers a vulnerability that leads to code execution.
The code within the exploit downloads several subsequent stages from the Command and Control server controlled by the cybercriminal, including other exploits for privilege escalation.
Once the exploitation is successful, a final payload is downloaded from the C&C server. The malware deletes the initial message and the exploit attachment.
“The malicious tool set does not support persistence, most likely due to the limitations of the OS,” Kaspersky said in the report. However, analysis of multiple iOS device timelines signals possible reinfection after rebooting the device.
Kaspersky added that the final analysis of the payload is not yet complete. The firm says the threat code runs with root privileges and implements a set of commands to collect system and user information. It can also run arbitrary code downloaded as plug-in modules from the C&C server.
SEE: Secure your Mac from hackers with these eight best practices.
Forensic analysis with the Mobile Verification Toolkit
Kaspersky explains that, because iOS devices cannot be inspected from the inside, in order to discover the threat, offline backups of the devices must be created. The backups are inspected using the Mobile Verification Toolkit, which enables forensic analysis of Android and iOS devices and is used to identify traces of compromise.
The mobile device backup will contain a partial copy of the filesystem and some user data and service databases. The timestamps of the files, folders and database records allow users to reconstruct the events happening to the device roughly. The MVT can generate a sorted timeline of events into a file called timeline.csv; this timeline can be used to identify the threat and its behavior.
While the attack covers its tracks by deleting the initial message and the attachment exploit, it is still possible to identify if a device has been compromised through the timeline analysis.
According to Kaspersky, the malware can also be transferred from an iTunes backup.
“If a new device was set up by migrating user data from an older device, the iTunes backup of that device will contain the traces of compromise that happened to both devices, with correct timestamps,” the firm said.
How to check iOS devices for malware traces
Following a set of procedures, iOS devices can be checked for traces of compromises.
First, to check an iOS device for any malware traces, a backup must be created. This can be done using iTunes or an open-source utility like idevicebackup2.
To create a backup with idevicebackup2, run the following command:
idevicebackup2 backup --full $backup_directory
Users may have to enter the security code of their device several times. Depending on how much data is stored on the iOS device, the backup process may take minutes or hours.
After the backup is complete, the MVT must be installed to process the backup. If Python 3 is installed in the system, run the following command:
pip install mvt
If the iOS device owner has enabled encryption, the backup copy will need to be decrypted using the following command.
mvt-ios decrypt-backup -d $decrypted_backup_directory $backup_directory
To run all the checks using the MVT, use the following command:
mvt-ios check-backup -o $mvt_output_directory $decrypted_backup_directory
The output directory will contain several JSON and CSV files. To analyze the timeline, the file called timeline.csv will be used.
Indicators of compromise in the timeline
When checking the file timeline.csv, Kaspersky found that the most reliable indicator of a compromise was a process named BackupAgent in the data usage lines. This process should not appear in a timeline under normal circumstances.
Note: The binary process BackupAgent2 is not an indicator of compromise.
When analyzing the timeline file, Kaspersky found the process BackupAgent is preceded by the process IMTransferAgent (Figure A).
Figure A
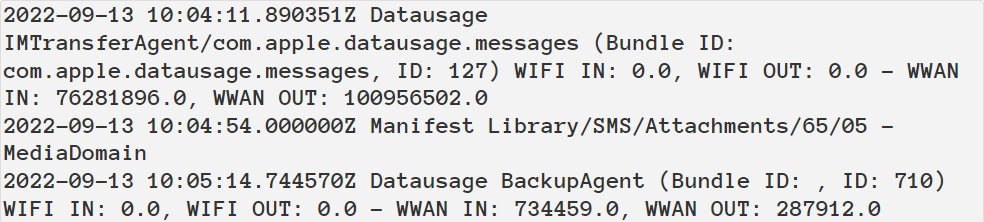
The IMTransferAgent process downloads the attachment, which in this case is the exploit. This download leads to the modification of the timestamps of multiple directories in the Library/SMS/Attachments. The attachment is then deleted, leaving only modified directories without actual files inside them.
Other indicators of compromises, if several are found to have happened within minutes of the timeframe, include:
- Modification of one or several files:
com.apple.ImageIO.plist,com.apple.locationd.StatusBarIconManager.plist,com.apple.imservice.ids.FaceTime.plist. - Data usage information of the services:
com.apple.WebKit.WebContent,powerd/com.apple.datausage.diagnostics,lockdownd/com.apple.datausage.security(Figure B).
Figure B
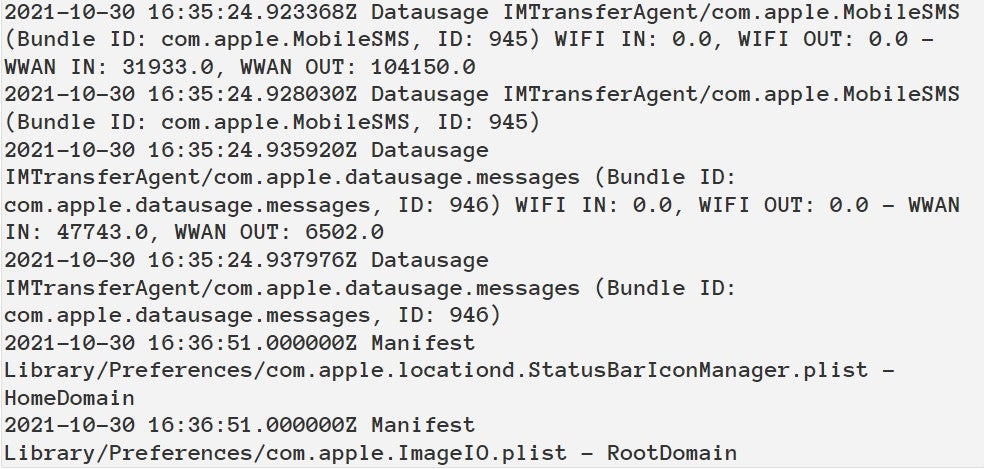
Another string of events happening within one to three minutes reveals the successful zero-click compromise via the iMessage attachment, beginning with the modification of an SMS attachment directory (but no attachment filename), followed by data usage of com.apple.WebKit.WebContent, followed by modification of com.apple.locationd.StatusBarIconManager.plist (Figure C).
Figure C
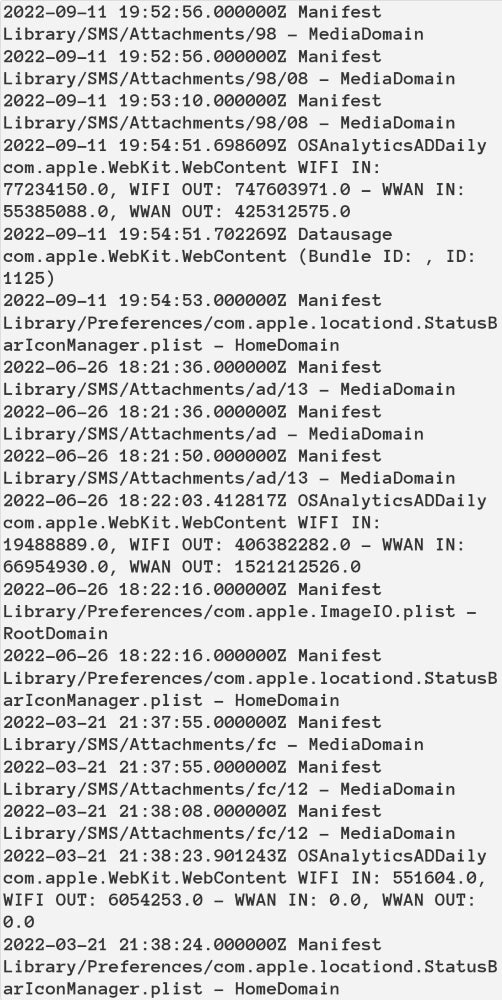
Network activity during exploitation
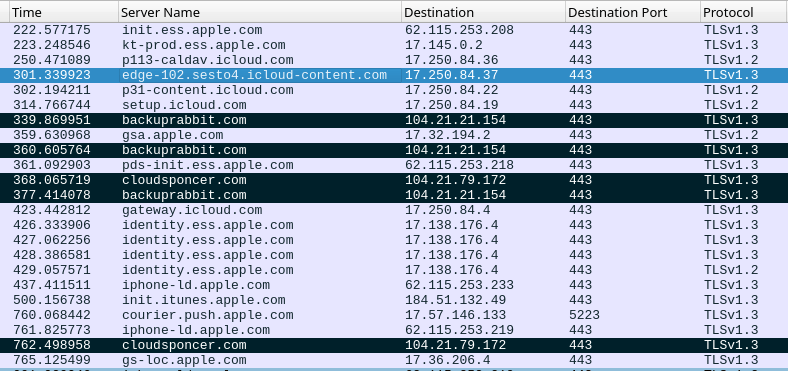
The attack also generates traces that can be identified on the network level. These traces show up as a sequence of several HTTPS connection events.
Analysis of the network shows activity due to the interaction with iMessage service in the domain names *.ess.apple.com, icloud-content.com, content.icloud.com to download the iMessage attachment containing the exploit and multiple connections with computers controlled by the cybercriminal with a significant amount of outgoing traffic (Figure D).
Figure D
The list of domains used by the exploits include:
- addatamarket[.]net
- backuprabbit[.]com
- businessvideonews[.]com
- cloudsponcer[.]com
- datamarketplace[.]net
- mobilegamerstats[.]com
- snoweeanalytics[.]com
- tagclick-cdn[.]com
- topographyupdates[.]com
- unlimitedteacup[.]com
- virtuallaughing[.]com
- web-trackers[.]com
- growthtransport[.]com
- anstv[.]net
- ans7tv[.]nett of outgoing traffic
How to stay safe from zero-click spyware
Kaspersky founder Eugene Kaspersky said on Twitter that the attack “transmits private information to remote servers: microphone recordings, photos from instant messengers, geolocation and data about a number of other activities.”
This would align the malware with other zero-click spyware such as Pegasus.
Following Kaspersky’s report on Operation Triangulation published on June 2, the firm released a special triangle_check utility that automatically searches for the malware infection. The tool is publicly shared on GitHub and available for macOS, Windows and Linux.
“Today, we are proud to release a free public tool that allows users to check whether they were hit by the newly emerged sophisticated threat,” Igor Kuznetsov, head of the EEMEA unit at Kaspersky Global Research and Analysis Team, said in a press release. “With cross-platform capabilities, the ‘triangle_check’ allows users to scan their devices automatically. We urge the cybersecurity community to unite forces in the research of the new APT to build a safer digital world.”
While the entire purpose of spyware is to act in the background without the user noticing it, there are several clear signs to keep an eye out for such as:
- Slowed-down network connection or suspicious high memory usage: Spyware needs to communicate with the attacker, transmit and send data, which can cause your phone to slow down, freeze or shut down.
- Phone battery drains more rapidly than usual: This is due to extra activity happening without your consent.
Unfortunately, protecting an iOS device against zero-click attacks is still complicated, as these are highly sophisticated malware. The best practice is to keep your iOS up to date. It’s also recommended to make the most of your built-in privacy and security settings.
[ad_2]
Source link



