[ad_1]
Cloud Security Posture Management tools are automated security solutions designed to continuously monitor and assess cloud infrastructures, services and applications for misconfigurations and compliance issues. These tools are more important than ever as more organizations now leverage the multicloud approach to cloud adoption, a practice that comes with configuration and security compliance complexities. In a recent report, CheckPoint ranked cloud misconfiguration as the biggest cloud security threat in 2023 for cloud users.
See also: Top 7 multicloud security solution providers for 2023
To address this challenge, many cloud-first organizations now deploy CSPM tools to help them monitor, identify, alert and remediate compliance risks and misconfigurations in their cloud environments. To determine which CSPM tool is best suited for your organization, TechRepublic has compiled a list of the top cloud security posture management solutions for 2023.
Jump to:
What is cloud security posture management?
CSPM software can help users maintain a secure cloud posture — how ready an organization can combat and bounce back from cyberthreats — by recommending best practices and enforcing security policies across all cloud accounts and services. These policies can include access controls, encryption settings, network configurations and more. By automating the enforcement process, CSPM software minimizes the risk of misconfigurations and accidental exposure of sensitive data.
Best cloud security posture management software comparison
The table below provides a comparison of key features available in each Cloud Security Posture Management Software.
| Compliance Reporting | Automated Remediation | Integration with Cloud Providers | Unified Dashboard | Pricing | |
|---|---|---|---|---|---|
| Orca Security: Best for cloud workloads | Yes | Yes | Yes | Yes | Contact Orca Security to get a quote. |
| Prisma Cloud: Best for multicloud environments | Yes | Yes | Yes | Yes | Contact Prisma Cloud for a quote. |
| Wiz: Best for managing identity-based exposure | Yes | Yes | Yes | No | Contact Wiz for a quote. |
| PingSafe: Best for real-time cloud infrastructure monitoring | Yes | Yes | Yes | No | Contact PingSafe for a quote. |
| Lacework Polygraph Data Platform: Best for inventory management and compliance | Yes | Yes | Yes | Yes | Contact Lacework for a quote. |
| CrowdStrike Falcon Cloud Security: Best for adversary-focused threat intelligence | Yes | Yes | Yes | Yes | Starts at $299.95/yr. |
| Tenable Cloud Security: Best for dev and production environments | Yes | Yes | Yes | Yes | Contact Tenable for a quote. |
1
ESET PROTECT Advanced
Protect your company computers, laptops and mobile devices with security products all managed via a cloud-based management console. The solution includes cloud sandboxing technology, preventing zero-day threats, and full disk encryption capability for enhanced data protection. ESET Protect Advanced complies with data regulation thanks to full disk encryption capabilities on Windows and macOS. Get started today!
2
NINJIO Cybersecurity Awareness Training
NINJIO prepares organizations to defend against cyber threats through their engaging, video-based training courses. They earned the highest score among providers named “Customer’s Choice” in Gartner’s 2022 “Voice of the Customer” Security Awareness Computer-Based Training report. Teams love NINJIO because of their Hollywood-style microlearning episodes, each based on recent, real-world breaches. Click below to get the full Gartner report and 3 free episodes, and see why everyone loves NINJIO.
3
ManageEngine Desktop Central
Endpoint Central is one super app to manage your enterprise IT, from endpoint management to end-user security. Streamline and scale every IT operation from device enrolling/onboarding to retiring for multiple device types across different platforms. Perform patching, distribute software, manage mobile devices, deploy OS, keep track of hardware/software inventory, and remotely troubleshoot end-user issues while shielding them from cyberattacks. Get a free 30-day trial on unlimited endpoints.
Best cloud security posture management software
Here is a rundown of the seven best CSPM software in 2023, highlighting their features, pricing plans, pros and cons.
See also: A fundamental guide to cloud security
Orca Security: Best for cloud workloads

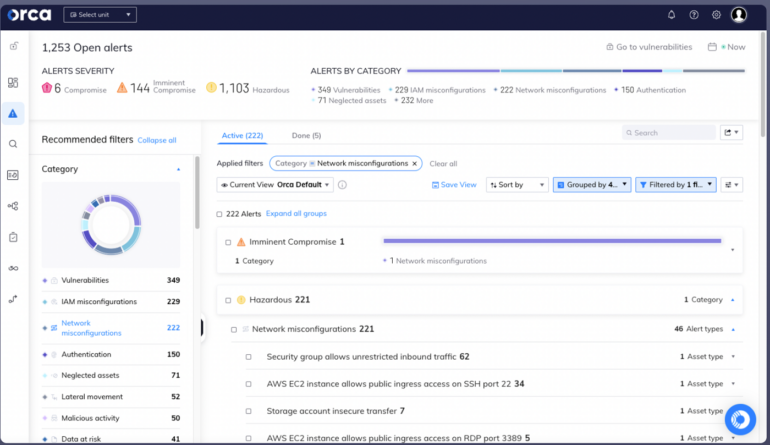
Orca presents users with a CSPM solution that scans their workloads and configures and maps the results into a centralized platform. It can analyze risks and identify situations where seemingly unrelated issues could lead to harmful attack paths. With these insights, Orca prioritizes risks, minimizing the burden of excessive alerts for users.
Orca also facilitates continuous monitoring for cloud attacks. It features a visual graph to give insight into an organization’s potential attack surface and the attacker’s end target within a cloud environment.
Regarding compliance, Orca provides compliance features that enable cloud resources to adhere to regulatory frameworks and industry benchmarks, including data privacy requirements. The platform unifies compliance monitoring for cloud infrastructure workloads, containers, identities, data, and more, all within a single dashboard.
Pricing
Orca offers a 30-day free trial. Contact Orca to get a quote.
Features
- Cloud compliance.
- Unified Data Model.
- Continuous monitoring.
- Orca Security Score.
- Attack path analysis.
- PII detection.
- Malware detection.
Pros
- Users can create personalized views of Orca’s Risk Dashboard.
- This solution offers a 30-day free trial.
- It helps organizations meet compliance with PCI-DSS, GDPR, HIPAA and CCPA.
- Users can generate comprehensive cloud security reports and share them across various channels.
- Users can write their own alert queries or use over 1,300 prebuilt system queries.
Cons
- No pricing information is available on its website.
Prisma Cloud: Best for multicloud environments

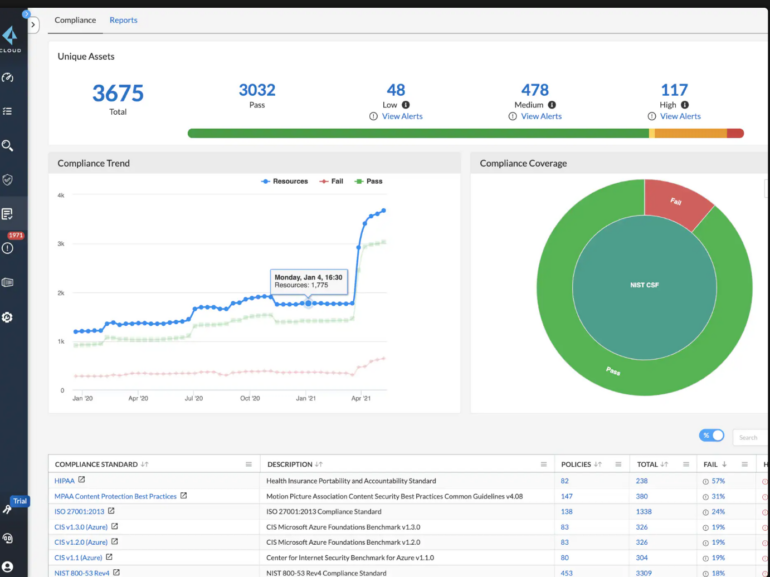
Prisma Cloud by Palo Alto Networks offers comprehensive visibility and control over the security posture of deployed resources in multicloud environments. The solution can help users implement instant configurations with over 700 pre-defined policies from more than 120 cloud services. That feature can aid organizations in correcting typical multicloud misconfigurations, preventing potential security breaches and developing custom security policies. With Prisma Cloud, users can also benefit from continuous compliance posture monitoring and one-click reporting, offering coverage for various regulations and standards, including CIS, GDPR, HIPAA, ISO-27001, NIST-800, PCI-DSS and SOC 2. The solution also provides custom reporting.
Prisma Cloud offers network threat detection and user entity behavior analytics features, allowing customers to identify unusual network activities, DNS-based threats and insider threats by monitoring billions of flow logs received every week.
Pricing
Contact Prisma Cloud for a quote.
Features
- Network threat detection.
- User entity behavior analytics.
- Data security.
- Compliance reporting.
- Configuration assessment.
- Automated remediation.
- Multi-cloud data visibility.
Pros
- Supports security and compliance management.
- Offers data governance with customizable policies.
- Integrated threat detection dashboards.
- Includes malware detection capabilities.
- Has a threat alert system.
Cons
- No pricing information on its website.
Wiz: Best for managing identity-based exposure

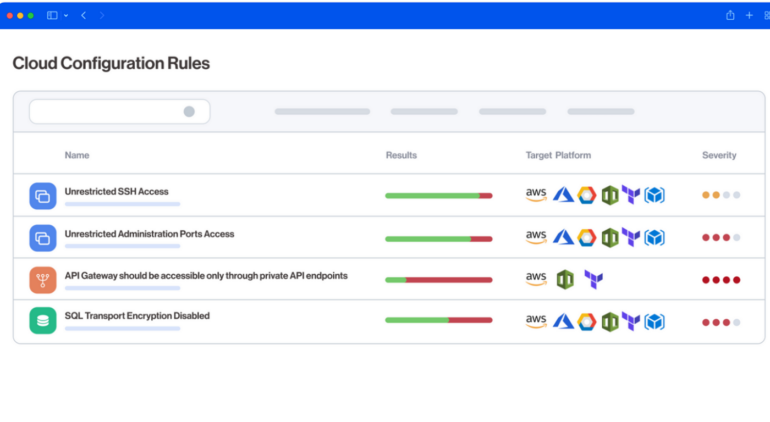
Wiz is designed to continuously detect and remediate misconfigurations across notable clouds, including AWS, GCP, Azure, OCI, Alibaba Cloud and VMware vSphere. By establishing connections to users’ cloud environments, Wiz delivers comprehensive visibility and actionable context on users’ critical misconfigurations, enabling teams to enhance their cloud security posture. The solution also offers network and identity exposure, which facilitates the identification of exposed resources through its graph-based network and identity engine.
With its automatic posture management and remediation feature, users can automatically assess over 1,400 configuration rules across different cloud runtimes and infrastructure-as-code (IaC) frameworks. Additionally, users can also build custom rules using the OPA (Rego) engine. Furthermore, Wiz continuously assesses users’ compliance posture against more than 100 built-in compliance frameworks. It also allows users to define custom compliance baselines and frameworks, offering flexibility and customization options.
Pricing
Contact Wiz for a quote.
Features
- Attack path analysis.
- Compliance reporting.
- Automatic posture management and remediation.
- More than 100 built-in compliance frameworks.
- Supports custom organizational compliance baseline.
Pros
- Network and identity misconfigurations are prioritized, focusing on critical areas.
- It allows users to define their own organizational compliance baseline.
- Teams can easily detect misconfigurations that pose the greatest threat.
- It offers built-in rules and automation.
Cons
- No free trial.
- No pricing information on its website.
PingSafe: Best for real-time cloud infrastructure monitoring

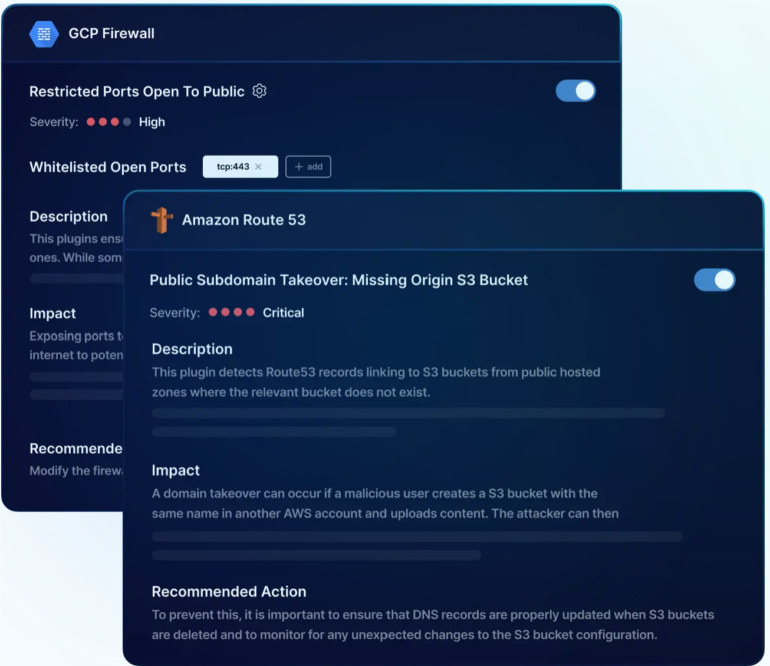
PingSafe automatically assesses over 1,400 configuration rules that detect cloud misconfigurations. It has features that allow organizations to create custom policies aligned with their unique security requirements, safeguarding sensitive data and resources against potential threats. The software also offers threat detection and remediation features to enable users to monitor the security posture of their cloud infrastructure and see possible remediation steps. There is also a context-aware alert system, which provides users with notifications when misconfigurations occur. With real-time continuous monitoring capability, the software can help security teams eliminate blind spots across their cloud environments.
Pricing
Contact PingSafe for a quote.
Features
- Context-aware alerts.
- Built-in rules.
- Real-time detection and remediation.
- Custom query support.
- Asset discovery and real-time monitoring.
Pros
- The agentless onboarding process eliminates cloud costs and reduces agent vulnerabilities associated with the agent-based approach.
- Continuous scanning of cloud assets provides users with a comprehensive view of potential vulnerabilities and threats.
- Organizations can tailor policies to their specific needs.
- Context-aware alerts provide users with actionable insights, allowing them to quickly address misconfigurations.
Cons
- No pricing information on its website.
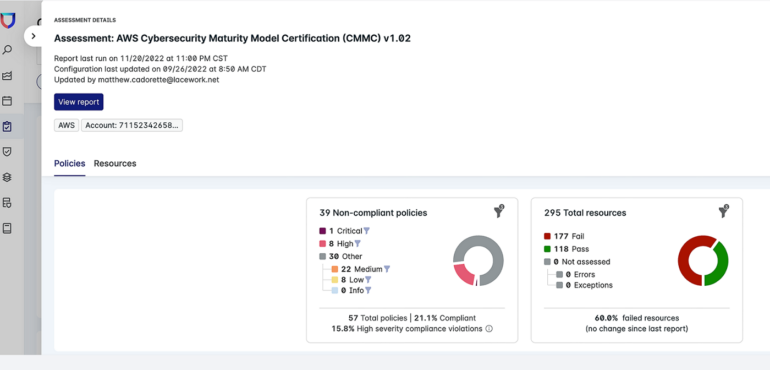
Lacework Polygraph Data Platform: Best for inventory management and compliance

Lacework Polygraph Data Platform allows for efficient inventory management of assets across users’ cloud environments. It keeps track of daily inventory changes, even for assets that no longer exist, ensuring an up-to-date understanding of the cloud infrastructure. With a unified platform for AWS, Azure, Google Cloud and Kubernetes configurations, Lacework offers users a consolidated view of their compliance across cloud providers. The platform also provides automatic monitoring and detection of misconfigurations and suspicious cloud activities. In addition, Lacework allows users to assess their posture and compliance against several pre-built policies, including PCI, HIPAA, NIST, ISO 27001 and SOC 2. Users can also set custom policies across cloud providers to meet their organizational requirements.
Pricing
Contact Lacework for a quote.
Features
- Pre-built and custom policies.
- Attack path analysis.
- Threat detection.
- Push button reports.
Pros
- Users can set custom policies across cloud providers.
- With push-button reports, users can quickly demonstrate their security posture and compliance to customers, partners and auditors.
- Users can create custom reports in multiple formats.
- It allows seamless integration with tools like Jira and Slack.
Cons
- No pricing information on its website.
CrowdStrike Falcon Cloud Security: Best for adversary-focused threat intelligence

Crowdstrike Falcon Cloud Security offers users agentless monitoring of cloud resources to detect misconfigurations, vulnerabilities and security threats. It adopts an adversary-focused approach, equipping users with real-time threat intelligence on over 150 adversary groups and 50 indicators of attack. This platform also provides multicloud visibility, continuous monitoring, threat detection and prevention capabilities while enforcing security posture and compliance across AWS, Azure and Google Cloud. In addition, Crowdstrike Falcon Cloud Security offers indicators of cloud infrastructure misconfigurations.

Pricing
Crowdstrike offers four pricing options with a 15-day free trial:
- Falcon Go: Starts at $299.95 per year.
- Falcon Pro: Starts at $499.95 per year.
- Falcon Enterprise: Custom pricing.
- Falcon Complete: Custom pricing.
Features
- Continuous compliance monitoring.
- DevSecOps integration.
- Agentless monitoring.
- Real-time threat intelligence.
Pros
- Simplified management and security policy enforcement.
- Offers guided remediation.
- Provides unified visibility across hybrid and multicloud environments.
- Provides real-time threat intelligence on adversary groups and indicators of attacks.
- Integrates with security information and event management solutions.
Cons
- Interface may be confusing for some users.
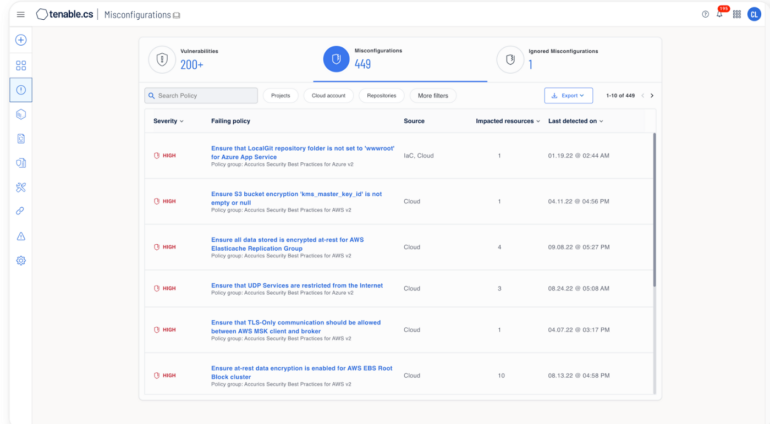
Tenable Cloud Security: Best for dev and production environments

Tenable Cloud Security provides its users with a framework for enforcing policies across multicloud environments. Offering multiple pre-developed policies, it allows users to apply industry benchmarks like those from the Center for Internet Security and other standards or create custom policies. With Tenable, security teams can scan their cloud environment to identify misconfigurations under a unified dashboard.
Some other key features that might interest users include an automated workflow that aids collaboration between DevOps and security teams, automated compliance status reporting, cloud inventory visibility and the capacity to prioritize risks based on their level of severity.
Pricing
Contact Tenable for a quote.
Features
- Unified framework.
- DevOps integration.
- Configuration drift tracking.
- Auto-remediation.
Pros
- This solution makes it easy to detect high-risk configurations that could lead to breaches.
- Users can easily enforce and report compliance with pre-packaged governance profiles.
- It offers risk-based scoring to determine threat severity.
- It facilitates collaboration between DevOps and security teams through automated workflows.
- Free trial is available.
Cons
- No pricing information on its website.
Key features of cloud security posture management software
The following features are commonly found in every top-quality cloud security posture management software.
CSPM tools help users maintain a secure cloud posture by recommending best practices and enforcing security policies across all cloud accounts and services. These policies can include access controls, encryption settings, network configurations and more. By automating the enforcement process, CSPM software minimizes the risk of misconfigurations and accidental exposure of sensitive data.
Compliance monitoring and reporting
Compliance with various standards and regulations is a top priority for any cloud-first organization. CSPM solutions facilitate compliance monitoring by regularly auditing cloud environments against industry-specific standards such as PCI DSS, HIPAA, GDPR, SOC 2 and more. These tools generate comprehensive reports and dashboards that help organizations understand their compliance status, identify gaps and take necessary actions to meet regulatory requirements.
Cloud asset inventory and visibility
Maintaining an accurate inventory of cloud assets is essential for effective security posture management. CSPM tools provide visibility into an organization’s cloud infrastructure, including virtual machines, storage accounts, databases and other resources.
Real-time cloud infrastructure monitoring
CSPM software provides continuous real-time monitoring of cloud users’ infrastructure. This allows organizations to promptly detect potential security threats and vulnerabilities, enabling them to respond quickly and mitigate risks effectively.
How to choose the best cloud security posture management software for your business
Selecting the right CSPM software is a critical decision that impacts the security and compliance of your cloud infrastructure. To make an informed choice, consider the following steps:
Assess your organization’s cloud posture management needs
Before going with any of the CSPM solutions, conduct an in-depth assessment of your organization’s cloud security requirements. Identify the specific challenges, compliance standards and cloud providers you work with to find a solution that best aligns with your objectives.
Evaluate key features
Evaluate each software based on its ability to meet your organization’s needs. Prioritize features that directly address your security concerns and streamline your cloud security management process.
Consider scalability
Ensure that the CSPM software you choose is scalable and can accommodate the expanding demands of your cloud environment.
Consider ease of use
User-friendliness is important as your IT team will be working with the CSPM software regularly. A straightforward and intuitive interface can enhance productivity and make it easier for organizations to navigate and implement security measures effectively.
Request demos and trials
Before making a final decision, you might want to get a hang of the product using its demo or trial version.
Methodology
To determine the best cloud security posture management software available in 2023, we first conducted an in-depth market analysis, identifying the leading CSPM solutions in the market today. Next, we assessed each software’s features, compliance capabilities and scalability to make sure they align with various organizational needs. We also analyzed customer feedback and reviews from Gartner Peer Insights to understand user experiences and the overall effectiveness of each solution.
Read next: How Generative AI is a Game Changer for Cloud Security
[ad_2]
Source link






