[ad_1]
The SYS01 infection chain uses DLL sideloading to steal information. Learn how to protect your business from this cybersecurity threat.

Morphisec, a security solution provider based in Israel, has reported that an advanced information stealer malware dubbed SYS01 is aimed at stealing access to Facebook business accounts and Chromium-based browsers’ credentials. Morphisec’s researcher has also seen the SYS01 malware attack critical government infrastructure employees, manufacturing companies and other industries.
This malware attack is similar to another campaign dubbed S1deload Stealer by Bitdefender, yet the final payload is not the same, leaving the question open as to who is behind the SYS01 stealer attack campaign.
Jump to:
SYS01 infection chain
The SYS01 malware attack starts by luring a victim into clicking on a URL from a fake Facebook profile, advertisement, or link to live streams, free applications, movies or games. When the user clicks on the lure, the download of a ZIP archive file starts.
The ZIP file contains a loader part and a final payload. The loader part consists of a legitimate application that is vulnerable to DLL sideloading. Once the victim runs the legitimate file, it silently loads a first payload contained in a DLL file contained in the same folder as the legitimate application.
As mentioned by Morphisec researcher Arnold Osipov, the loader might be any kind of executable file, such as Rust and Python executables. Yet, the behavior is always the same when run: It executes the code from a malicious DLL file contained in the ZIP file.
The malicious DLL in turn executes an Inno-Setup installer that decompresses and drops PHP code responsible for stealing and exfiltrating information (Figure A).
Figure A
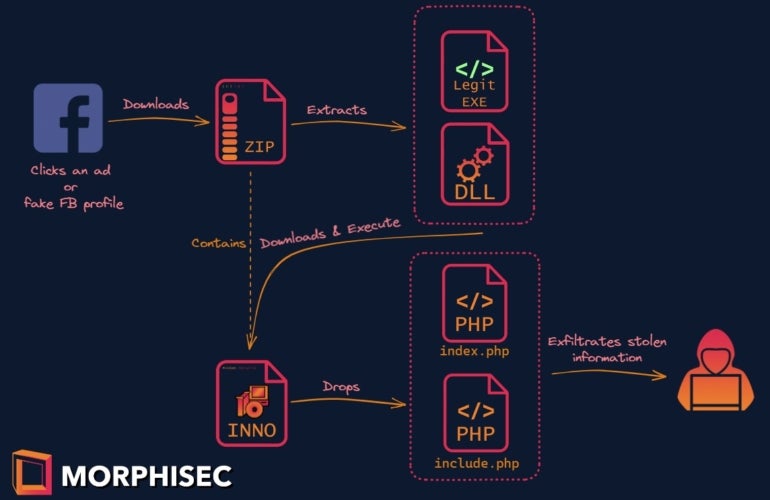
Different scenarios might happen with the loader part. For starters, the ZIP file might contain the necessary second stage payload. If it is not in the ZIP file, the second stage payload is likely being downloaded from an attacker-controlled C2 server before being decoded and executed.
SYS01 information stealer
After the loader is executed successfully, the Inno-Setup installer is executed. The installer drops a PHP application with additional files:
- Index.php is in charge of the main malware functionalities.
- Include.php establishes the malware persistence via scheduled tasks; it is the file executed by the installer.
- Version.php contains the malware version.
- Rhc.exe hides the console window of started programs, enabling the malware to be stealthier by not showing specific windows to the currently logged-in user.
- Rss.txt is a base64 encoded file, which contains an executable file written in Rust. The executable gets the current date and time and decrypts Chromium-based browsers encryption keys. The date and time is fetched by the malware to know when to establish persistence in scheduled tasks.
As noted by Osipov, older PHP files were not obfuscated, yet the newer versions of the malware have been encoded using commercial tools ionCube and Zephir.
Once the malware is running, it sets up a configuration array containing various information, including a list of C2 servers randomly chosen and used at every execution of the malware. The malware is also able to download and execute files and commands, in addition to being able to update itself.
SYS01 steals particular data
SYS01 stealer is able to get all cookies and credentials from Chromium-based browsers.
The malware checks if the user has a Facebook account. If the user is logged in to that account, the malware queries Facebook’s graph application programming interface to get a token and steals all of the victim’s Facebook information. All of the stolen information is exfiltrated to a C2 server.
How to protect from the SYS01 malware threat
DLL sideloading is possible because of the DLL search order implemented in Microsoft Windows. Some developers have this problem in mind when programming their software and create code that is specifically not vulnerable to this technique.
However, Morphisec noted that most programmers do not have security in mind when developing, so companies need to add more protection against that technique:
- Set users’ privileges, so they cannot install third-party software that might exploit DLL side loading.
- Monitor warning signs for DLL sideloading. Unsigned DLL files used by signed executables should raise such warnings, as well as suspicious loading paths.
- Use security tools such as DLLSpy or Windows Features Hunter to try to detect DLL sideloading. Resources such as Hijack.Libs can also be useful, as it lists a lot of applications vulnerable to DLL sideloading.
- Keep operating systems and all software up to date and patched in order to avoid being compromised by a common vulnerability.
- Train employees to detect common social engineering tricks and to be aware of the risks of downloading third-party content from the internet, especially pirated software which often contains malware loaders.
Read next: Security awareness and training policy (TechRepublic Premium)
Disclosure: I work for Trend Micro, but the views expressed in this article are mine.
[ad_2]
Source link



