[ad_1]
Learn how IPFS is used in phishing attacks and why it’s especially tricky to remove the impacted pages, as well as how to protect from this security threat.

The fraudulent use of the InterPlanetary File System seems to have increased recently, as reported in new research from Kaspersky. IPFS has been used by cybercriminals for email phishing attacks since 2022.
Jump to:
What is IPFS?
IPFS is a peer-to-peer network protocol designed to provide a decentralized and distributed web. Unlike traditional web protocols that rely on centralized servers, IPFS allows users to share and access files without depending on any central authority.
IPFS identifies files by their content rather than their location. Each file is given a unique cryptographic hash called CID; the content identifier can be used to retrieve the file from any node on the network that stores a copy. This makes it easy to distribute and access content, even if the original source is offline or unavailable.
IPFS also uses a content-addressed system, which means any changes made to a file will result in a new hash. This ensures files remain immutable and tamper-proof.
Accessing IPFS can be done via a dedicated application programming interface or gateways, which provide access to IPFS content and is usable for any web browser.
The URL to access the gateway contains the CID and the gateway but may vary from one gateway to another. For example, it could be:
- https://gateway/ipfs/CID
- https://CID.ipfs.gateway
How IPFS is used in phishing attacks
In a usual phishing case, the target is enticed to visit a fraudulent phishing page that will steal their credentials and possibly their credit card information; however, this fraudulent page can be hosted on IPFS and accessed via a gateway.
The use of such a system allows attackers to reduce the costs of hosting the phishing page and makes it harder to remove the fraudulent content from the internet because it might reside on several computers at the same time.
In case a user has clicked on a phishing link and provided their credentials, it is important that the user changes their password as soon as possible and checks to see if there has been any malicious activity using that account.
Targeted phishing attacks also use IPFS
Most IPFS phishing attacks are not too original when compared with usual phishing, yet in some cases, IPFS is used for complex targeted attacks, according to Kaspersky (Figure A).
Figure A
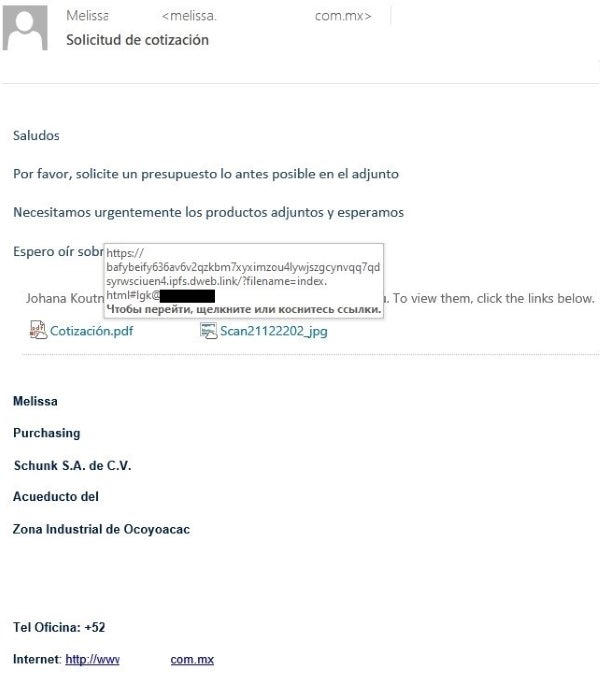
As can be seen in Figure A and described by Kaspersky, “the attacks were leveled at corporate procurement departments, the letters coming from sales managers of existing organizations.”
Phishing page removal is trickier for IPFS content
Usual phishing pages can be taken down by asking the web content provider or owner to remove them. That operation can take quite a bit of time depending on the host, especially when it is stored on bulletproof providers, which are illicit hosting providers who tell their customers they do not reply to law enforcement requests and do not take down content.
Takedown operations on IPFS content are different in the way the content needs to be removed from all nodes.
IPFS gateways’ providers attempt to combat those fraudulent pages by regularly deleting links to those files, yet it does not always happen as quickly as the blocking of a phishing website. Kaspersky’s researcher Roman Dedenok wrote on March 27, 2023, that Kaspersky has “observed URL addresses of IPFS files that first appeared in October 2022 and remain operational at the time of this writing.”
IPFS phishing statistics
As of late 2022, there were 2,000–15,000 IPFS phishing emails a day. In 2023, IPFS phishing began to increase in Kaspersky’s volumetry, with up to 24,000 emails a day in January and February; however, after that increase, the numbers came back to almost the same values as in December 2022 (Figure B).
Figure B

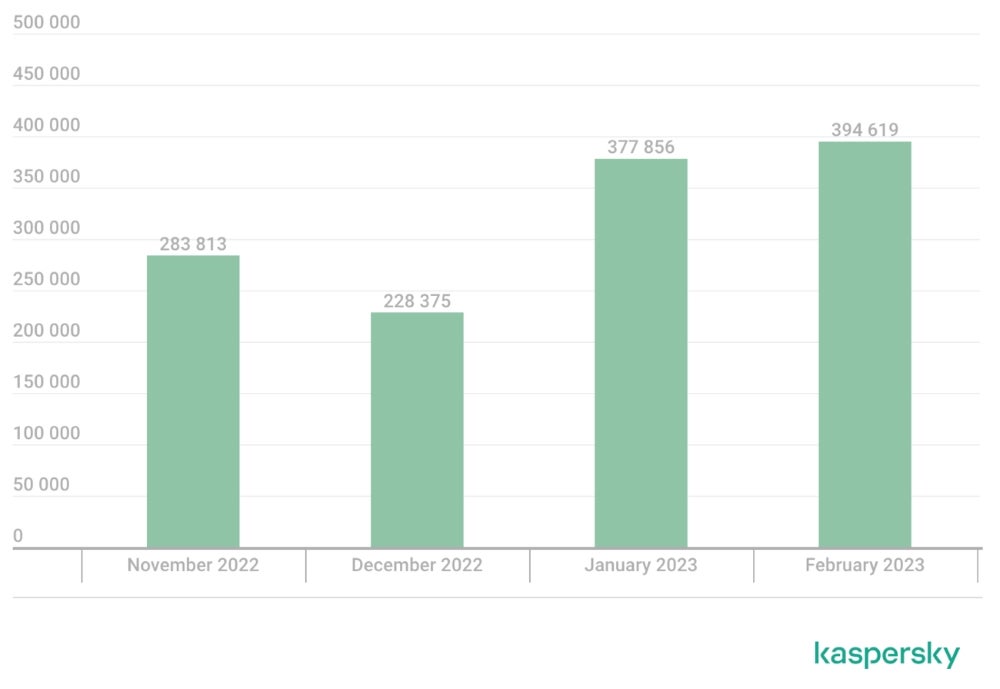
Monthly statistics show a busy month in February with close to 400,000 phishing emails, while November and December were approximately between 228,000 and 283,000, respectively (Figure C).
Figure C
How to protect from this IPFS phishing threat
Anti-spam solutions such as Microsoft Exchange Online Protection or Barracuda Email Security Gateway will help detect IPFS phishing and block links to it, just like for any usual phishing case.
Users should be educated about phishing emails or any kind of phishing link that could be sent to them via different ways including instant messaging and social networks.
Implement multifactor authentication to protect against unauthorized access. This will make it more difficult for attackers to gain access even if they have obtained login credentials through phishing.
Disclosure: I work for Trend Micro, but the views expressed in this article are mine.
[ad_2]
Source link



